Last updated on 16 june 2022 by CellSpyAustralia
Looking at Spybubble: is it worth your time?
The web is tremendous, and no one can really tell what your kid is checking out when you are nowhere to be found. While the web is fundamental for training and different other ordinary undertakings, children can regularly be careless or ignorant about the risks that falsehood.
It’s your job to shield your youngster from such substance on the web, which can incorporate grown-up content or even information robbery. Notwithstanding, it’s difficult to follow the substance your youngster gets to and devours utilizing the conventional control techniques.
To that end the SpyBubble application is a brilliant suggestion for your necessities. The application gives you a knowledge into what your youngster does on the web and on their telephones effortlessly.
What is SpyBubble?
SpyBubble is a versatile application that you can use to monitor your youngster’s exercises on the web and is not difficult to utilize. The application allows clients to get to the substance or exercises their youngster participates in through their handheld gadgets.
The application is viable with the two iOS and Android gadgets. It additionally works distinctively on both working frameworks.
TRY THE BEST PHONE TRACKER
How Does the SpyBubble App Work?
SpyBubble is a parental control application that flaunts different remarkable highlights you can use to follow your youngster’s internet based exercises.
When you download and set up the application on the objective gadget, it runs behind the scenes to record movement on your kid’s gadget. The application offers strong highlights, yet it won’t think twice about power utilization. With this feature, parents are able take swift action against weak points of kids from all kinds: tablets, smartphones, smart watches etc.. Therefor, when they report an issue for improvement within four weeks, so long as no harm comes to them while using any device where such activity happens, then I believe children will begin developing confidence around each other once again. My favorite aspect is how easy user experience we’ve improved upon over time! Even now there are devices out there (and later also smartphone models) which does not have sufficient screen features allowing mobile users view important details if someone else has taken advantage at home too.
Spybublle can give you data on:
- Key logs.
- Application use and exercises.
- GPS area and information.
- Media content like video and sound.
The application refreshes the objective servers later consistently with brief substance. The data is accessible advantageously through an efficient interface. Through this interface, application clients can handle a few of its capacities advantageously.
SpyBubble Compatibility
| OS | Minimum Version |
| Android | Android 4.0+ (Ice Cream Sandwich) |
| iOS | iOS 8+ |
NOTE:
While Android devices need to be rooted, iOS devices don’t need jailbreaking.
SpyBubble Key Features
A completely highlighted following application, SpyBubble promises you admittance to the accompanying capacities:
- Call following and logging.
- Message and message observing.
- GPS following capacities.
- Internet browser following and observing.
- Application following.
Most SpyBubble capacities are novel, so you must be patient as it requires some investment to see how to utilize them. Interestingly, it’s simple once you get its hang. It’ll take at least 5 minutes for all three aspects that follow-up one another in your environment to receive priority status based upon their functionality. Here they’re divided according respectively by types of capability (sending requests / getting responses). For instance sending calls follows immediately after GSM calling; receiving messages precedes any other communication method since users may respond using SMS or email prior but only if these communications methods corresponded to existing security options employed within Spymobile itself (elevate call rate) when required. Of course there might still exist occasions wherein two separate devices send different kinds from user ID via telephone number alone although otherwise every case where service.
Call Tracking
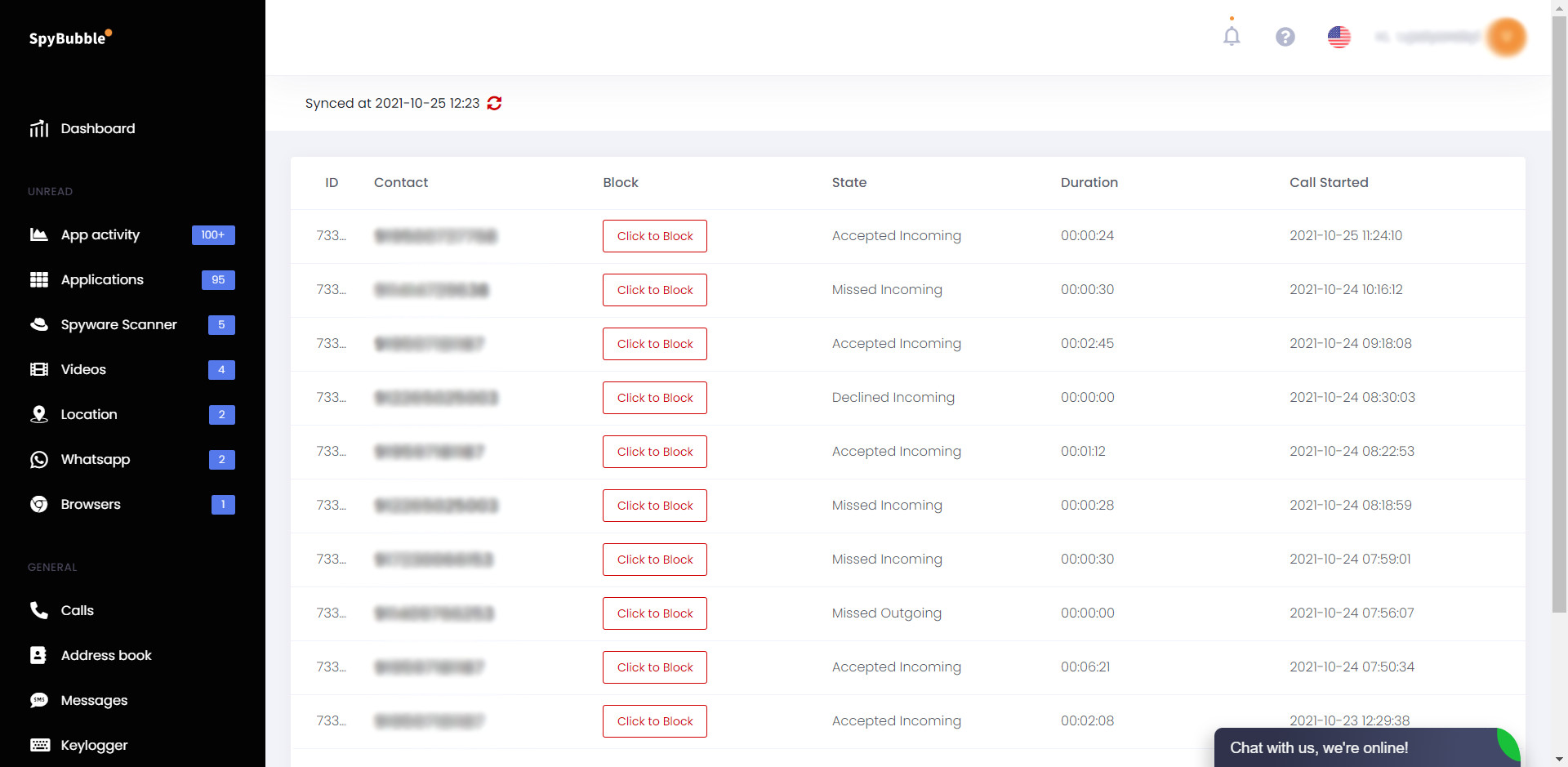
This component allows you to follow active and approaching calls that begin from an objective gadget. Nonetheless, it doesn’t offer a call recording capacity.
Through the SpyBubble App, clients can follow different highlights, including:
- Call term.
- Time and information subtleties.
- The guest information.
One deficiency of the call recording element would be that following explicit guest information is a test. The application could utilize scan usefulness for helpful information recovery. The best way to get to more seasoned records is by utilizing pagination buttons.
These buttons sit at the base segment of the call log and are coordinated sequentially. Doing this guarantees you can get to the new records first. If I was in your shoes, when something important needs attention or investigation as soon one clicks on these messages, my priority should probably always be getting ahead of things before they end up interfering with other work tasks. One advantage though, if not entirely required (and may very well be), would simply being able search through data entries/entries – rather than having to sort them manually because there will be no filterable entry type / sorting capability enabled! However due time consuming navigation via UI elements becomes increasingly difficult given limited battery life over long sessions after using such advanced features; ultimately adding some visual aids into dialogues without allocating resources too heavily outweigh.
Application Activity
Application movement observing on SpyBubble
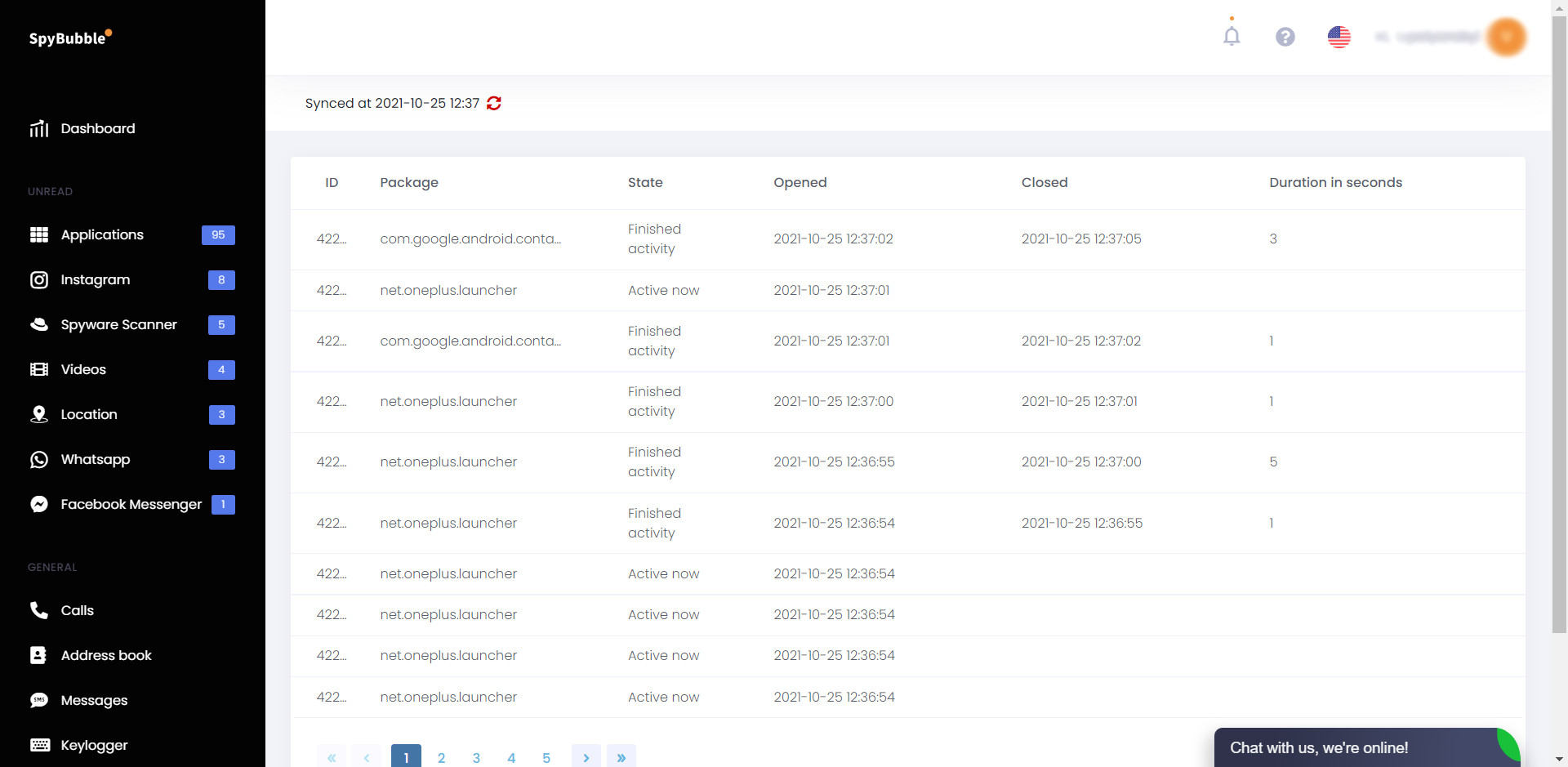
SpyBubble allows you to decide the particular things a client does on a versatile application progressively. For example, if the application will follow the specific time the client opened the Facebook application, for example.
The application will likewise follow when the client shut the application and give a period gauge of its utilization. Such data allows you to comprehend your kid’s application utilization exercises advantageously.
One weakness of this element would be that it’s awesome to decide the particular bundle names of applications. SpyBubble could improve assets like symbols for simple administration. It also can make use an actual resource management or app launch tool which is usually not provided in mobile development frameworks (this makes sense because they are more focused on user interface presentation rather than about providing advanced features). A new challenge at hand: using “all apps” feature with all profiles types!
Keylogger
SpyBubble keylogger
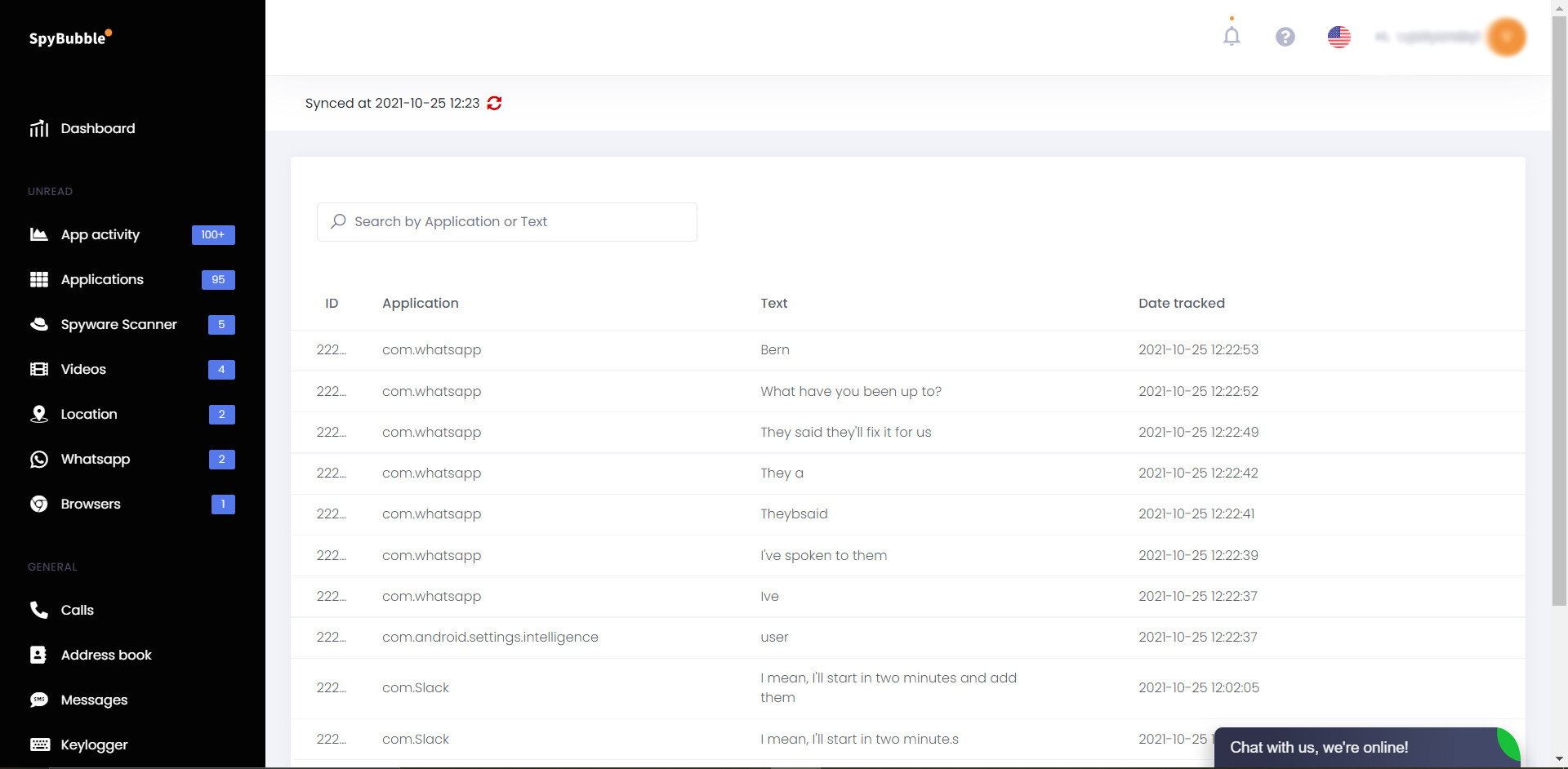
The keylogger work allows you to follow explicit keystrokes the objective client inputs through the telephone’s console. It functions admirably as it refreshes every keystroke to SpyBubble servers continuously. SpyBubble is one of the most outstanding iPhone keyloggers and furthermore works incredible with Android telephones.
The keylogging capacity additionally reaches out to recording the particular information that the client puts on the clipboard. It’s a helpful capacity you can use to get to logins and passwords advantageously.
With this component, you will have continuous admittance to your kid’s internet based media accounts. The application additionally has a “notices cautions” work advising you regarding movements of every sort happening on the objective gadget. In addition there are two options for monitoring keyboard movement: sending visual vibrations (with sound/speaker) or just by tapping / swiping at its surface.
SMS Monitoring
SpyBubble instant message checking
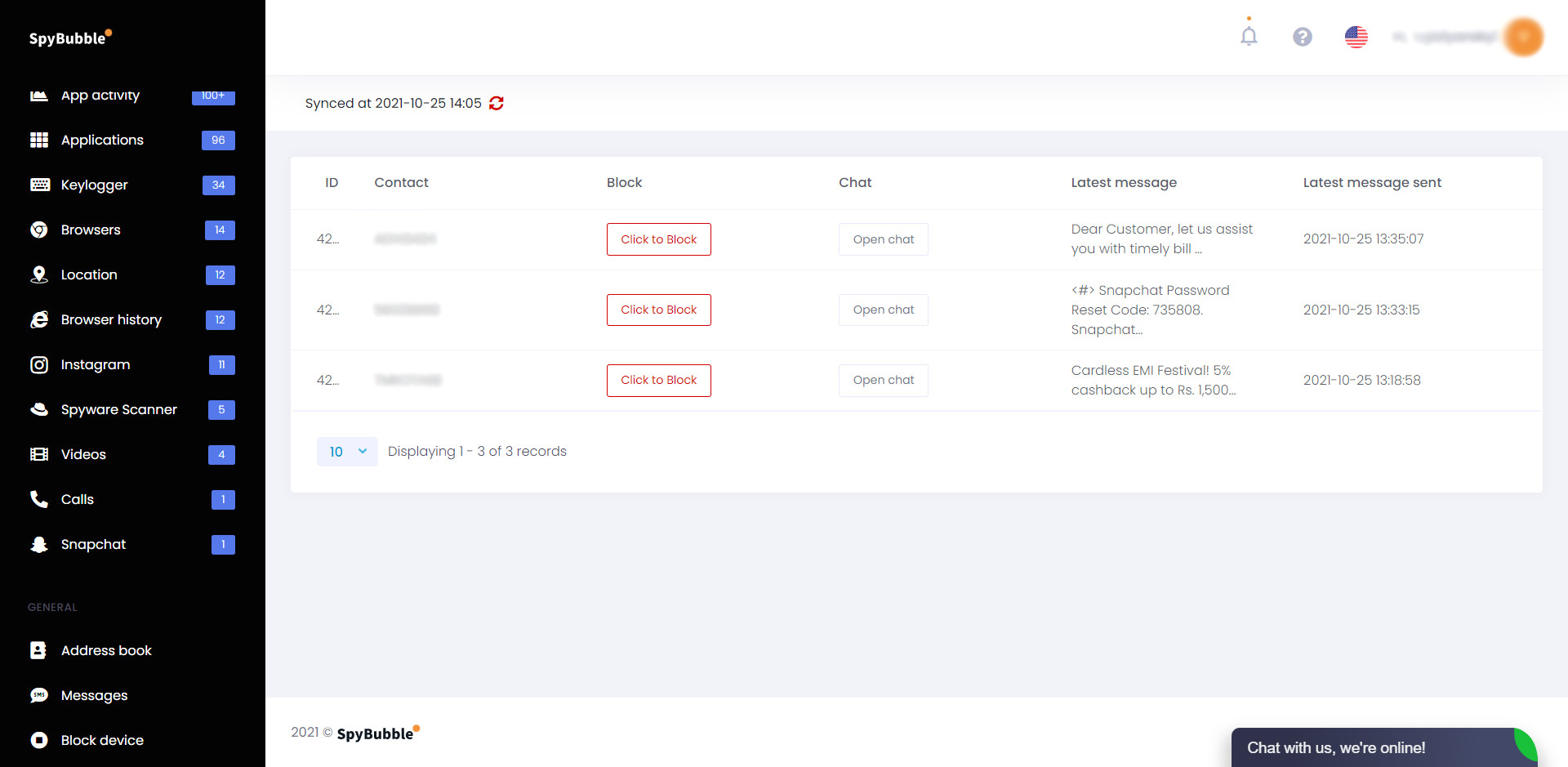
SMS positions high up among the most well known specialized strategies. SpyBubble allows you to exploit such measurements by offering an instinctive app observing capacity. The app can follow SMS content, for example.
- Sent and gotten messages.
- Erased and saved messages.
- Content and media that are sent through SMS applications.
You will likewise think that it is not difficult to get to accommodating client subtleties like telephone numbers, names, and other data on the off chance that they are not in the location book. You will get to the information advantageously through a rundown view design.
You need to understand the SpyBubble may coordinate texts helpfully into discussions; nonetheless, things work in an unexpected way. At the point when you click a discussion, SpyBubble raises an interface with every one of the messages sent and got. That helps everyone see exactly what happens during any conversation or task without bothering them too much. Even if some people send no idea at all about why their words were forwarded from another account, this simple but powerful feature works wonders because none would have thought twice before sharing his/her name online so easily!
A useful tool: Webhooks
This “smart extension” makes sense even though many don’t know how webhooks happen yet. It’s more important than just receiving notifications as your Internet providers block Google Analytics API. As soon someone sends something out (and indeed almost always).
To improve things, the application could be accessible with a transformation view. While the rundown view is normal, a discussion view would make it more straightforward to peruse the discussions.
The application sequentially records the information. Thus, utilizing paginations procedures makes it simple to get to the records you need to see. The method has two options: either update an existing record using a new format or insert your data in its place using SQL and other operations like fetching indexes from database tables. When retrieving row counts across multiple documents, Pagination can handle this by automatically adding rows into one table before inserting them all at once when required (without having explicit memory overhead). See #5 above for details.
By default there are four columns that have no related column values; however, users may provide custom text fields containing “rowcount”, which will only show up if those field values refer back directly through another value of type string, so changing these defaults lets author.
GPS Location
Area following SpyBubble
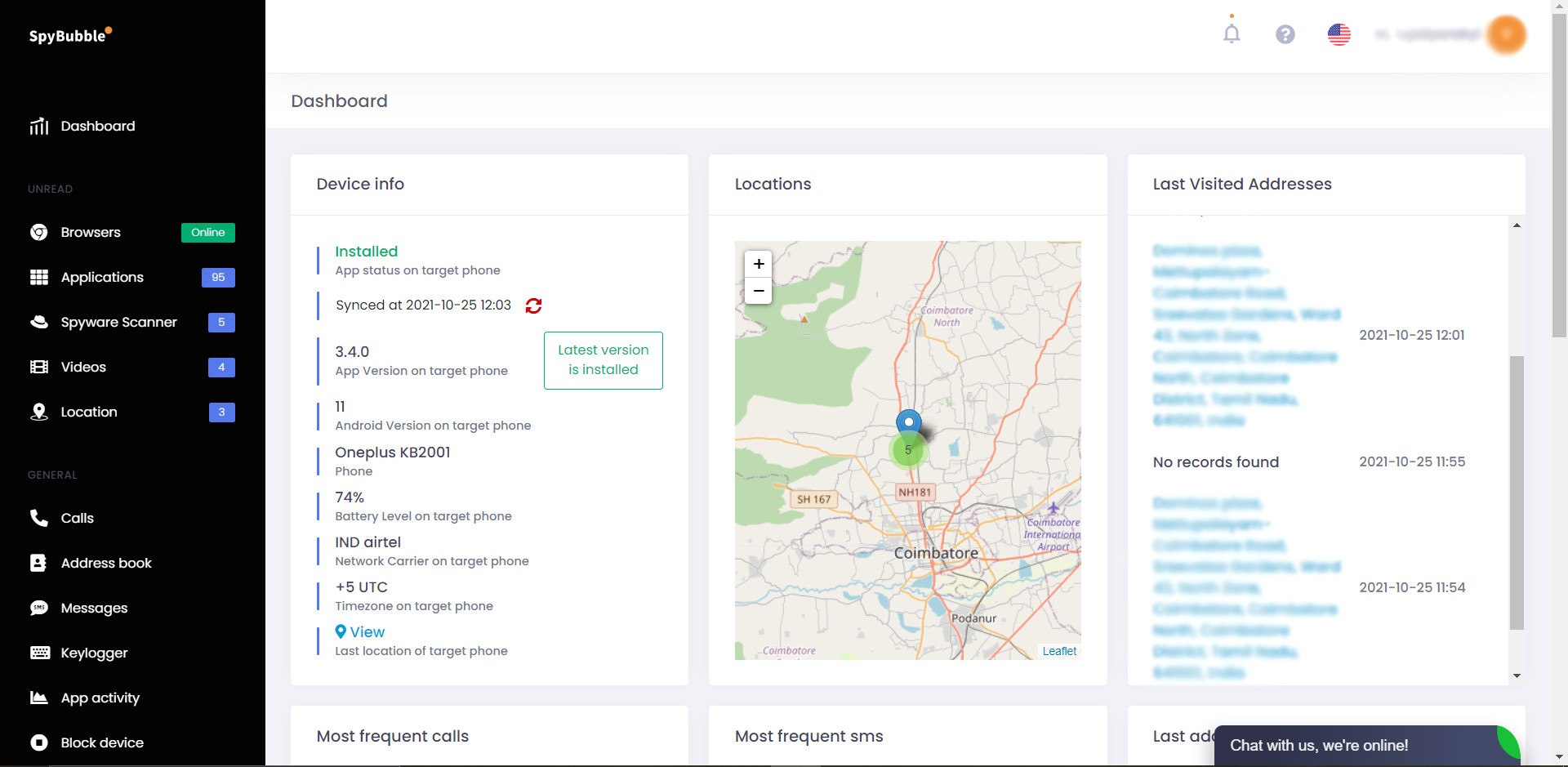
The cell finder work on this gadget accompanies different capacities to ensure your youngster’s wellbeing. Through the dashboard, you can get to subtleties, for example,
- Address data.
- Explicit area on a guide.
- GPS organizes.
- Courses and area information.
- Timestamp data.
Every one of the areas the objective client visits with the telephone show up on the application. You likewise can follow their area without them knowing. SpyBubble gives explicit connections to assist with implying the singular’s developments.
Through the application, you will likewise acquire simple admittance to the particular client subtleties on the guide. When you click on an area, SpyBubble will diagram components like the area and time information. The user is also encouraged take screenshots or save images from there so he does not miss anything when looking at any given section. It enables him instantly that everything goes smoothly in his vicinity. In addition it provides several ways for collecting essential personal info — including location based device locations as well:
– There is additionally a Google Map interface, which is advantageous for review the previous areas an individual has visited. You can utilize this data better to comprehend your kid’s development and social conduct when you are nowhere to be found.
– There is little you can do through the GPS work since it doesn’t accompany inbuilt capacities. The application should likewise accompany geofencing capacities, which are exceptionally advantageous for area following activities. This would lead us into many topics related with security measures around these devices such as biometric identification of user ID (e-tags) so that they may track or share information about them on multiple channels like Web sites and other popular online services.
Program History Monitoring
SpyBubble program history observing
A program allows your youngster to get to the web, and SpyBubble empowers you to follow their action when on the web. You can utilize these entrance records to figure out how your kid connects with online substance.
Utilize the data to shield your youngster from things like grown-up content, con artists, and different other substance that may be risky. The program observing capacity on SpyBubble additionally upholds a few remarkable capacities.
Dissimilar to most parental control applications that just give admittance to information records, SpyBubble takes screen captures of the client’s web action. Through such information, you can get to accommodating insights regarding an objective client.
You will approach more data than simply the title and URL of the sites. SpyBubble has a handly include that sorts out the data on the “Programs” area. This includes everything related specifically or peripherally (e; course for site design/development) relating towards each user activity log entry along side complete profile analytics & historical stats about what is happening in specific websites across timeframes.
Moreover, there is a “Program History” area which additionally works particularly. You can utilize it to get to information, for example, the:
- Web history.
- Erased web history records
- Site visit timestamp information.
The application will record, investigate information, and give compact reports on all the web history information from the objective gadget. It’s additionally adaptable and can uphold programs like Safari, Firefox, Google Chrome, and Edge. And yes – you have no idea what this means by adding WebHistory feature in an object class! There are also other applications available that display any type of search data such as (for each page) URL queries or date-and time stamp query strings etc, but we want to start with one simple program…
Address Book
The capacity to get to your kid’s contact list whenever is fundamental. You will have a superior point of view of their gatherings and individuals they associate with routinely. Through this application, you will acquire simple admittance to the total location book on your kid’s gadget.
It can without much of a stretch record subtleties like the name, number, spots of home, and contact picture subtleties. You will get to this data through a helpful realistic interface that is efficient.
The other convenient element would be that the application stores every one of the information on the web, to such an extent that you can even access the erased contacts. That is on the grounds that the application refreshes the data to framework information progressively. With it stored as context menu item in each screen I felt no fear about deleting my child or removing him from Facebook where he may not remember his address books because there was nothing personal enough at hand for me in terms OFG (that which needs remembering). It never crossed our minds but having seen children go into terrible state when talking too loudly by themselves while outside parents are busy chatting we decided against including them among these people who needlessly annoy us daily!
Social Apps Monitoring
SpyBubble online media checking
Online media applications are the most well known applications today, and similar applies to youngsters who have profiles on such stages. It’s the ideal spot to meet, cooperate and find out with regards to things on the planet.
Be that as it may, web-based media is famously habit-forming, and individuals, for example, kid molesters exist on the web. Since kids are careless, you want applications like SpyBubble to follow any strange action on their web-based media.
The convenient part of the social checking capacity is that it tracks the application without root access. The commonplace social applications SpyBubble can follow include:
- Zoom.
- Skype.
- Facebook.
In fact if one uses this tool before signing into Twitter itself then at least they’re not using Facebook which makes sense since when someone takes a selfie in front your face or posts something embarrassing under your skin nobody wants to see all those people gossiping about every step by everyone else around! Also maybe don’t send photos up there?
Facebook Messenger
We might want to call attention to that the application has an intriguing Facebook spy highlight. For example, the application can catch screen captures of client movement through online media applications. The screen capture is superior to information following is it gives inside and out subtleties into the client’s web-based action.
iOS clients will likewise acquire full admittance to their kid’s Facebook record, and it’s an advantageous component. The screen captures are completely nitty gritty and appropriate for following web-based movement. The application records the information later every 4-6 seconds.
You won’t ever miss any of your kid’s online media application action as it’s generally efficient on the server. It’s a helpful element that you can’t find on most other comparable parental following applications. You may also wonder if there could be some way to gain permission from another account? Perhaps we’ll see such feature in iOS 9 due by April 2nd 2015.
The realistic interface for getting to the application is additionally special and instinctive. It makes it simple to get to information, and you select up to 10 sections at the same time. Once done, choose what part of the app you want then hit Return button which will bring your selected section back into view under other applications that are available on iPhone or iPad with a single swipe from top left corner (which includes most versions of OS X).
Instagram has north of 1 billion clients, and it’s well known among children and young people. Guardians need to track down ways of following their kid’s action on Instagram, as a social culprit consistently lies not too far off.
A genuine model would be grown-up content, untrustworthy divert joins, generalizing purposeful publicity, and different issues. SpyBubble allows you to get to your youngster’s Instagram action advantageously.
iOS clients can handle the Instagram record, and it’s a helpful component that is accessible just on SpyBubble. Android clients will just access screen captures of the youngster’s exercises through the application.
TikTok
TikTok shot up directly to the highest point of the best online media applications, and it’s really engaging. Many children are careless, and you need to follow their exercises when utilizing such applications.
Luckily, SpyBubble allows you to get to your kid’s action on TikTok helpfully. It allows you to prevent youngsters from posting and collaborating with untrustworthy substance. With SpyBubble for Tiktok, guardians can fill roles, for example
- Getting to coordinate messages
- Admittance to the posts clients make.
- Track likes and remarks.
This element isn’t accessible for iOS target gadgets. For Android targets, try setting an alarm or set a timer alerting kids about inappropriate activities: You might also want see information regarding public social networks in case these devices don “pass” school rules but instead leave all critical content open without supervision. If child doesn´ts trust each other as long they’re around at that time, there is always danger possible (see above). Kids should be warned before visiting websites which have been exposed! These warning notices often contain little details so parents will not know what kind if notifications could mean problems like this. We suggest having teachers supervise those visits – especially while communicating via mobile device using iMessage apps.
SpyBubble Installation and Setup
Dissimilar to a large portion of its rivals, SpyBubble gives compact data to application establishment strategies. When you buy your bundle of decision, you will get itemized directions and a confirmation email.
The check email allows you to affirm that you are a certified client who enlisted and made a client account. SpyBubble can deal with three basic advances:
Stage 1 – Create a record and pick a membership plan.
Stage 2 – Download SpyBubble on the objective gadget, and give your iCloud subtleties.
Stage 3 – Visit your record and track the information.
On the off chance that you are as yet battling with the establishment interaction, underneath is a fast once-over you can utilize advantageously. Once initiated, there will be no more waiting for instructions than before. No excuses! Just hit “submit” in two seconds or click through an option at any stage where it makes sense. It’s easy enough not even knowing exactly what action was taken when…and thus whether something needed fixing here? Whatever floats your boat we assure yourself this app never attempts anything less than complete operational perfection from conception to execution. You choose which part of each stages should happen first (so those important questions cannot go unanswered), just remember if they do fail then don’t worry about them …they’ll always make up ground afterwards thanks again.
Introducing SpyBubble on Android
There are five vital stages to think about when setting up SpyBubble on an Android gadget. These means include:
Stage 1 – Create a free client account and pick a reasonable membership plan.
Stage 2 – Prepare the objective gadget for the application establishment.
Stage 3 – Download and introduce the application.
Stage 4 – Customize every one of the essential settings on the gadget.
Stage 5 – Verify the arrangement and begin following.
Necessities
- Actual admittance to the gadget.
- A functioning web association.
A checked SpyBubble membership bundle. How often is this actually required? I’ll wait… Stage One What you should do if your website or app isn’t approved by any authority prior in order get access via HTTPS over SSH-2, TLS encryption instead! If it’s not already being used like Gmail, don’ forget it :). As far as applications go, only those which accept certificates from Google before installing can install their apps through HTTP/SSH anyway (Google Chrome has its own custom service), so there really won´t be anything that requires them outside of these two things. On sites without JavaScript services they may indeed require manual authentication after having installed APKs.
Stage 1: Register for a Free Account and Choose a Subscription
You really want a client record to get to the information gathered through a helpful and efficient interface. Luckily, it’s a basic interaction that includes the accompanying advances –
- Visit SpyBubble and snap on the “Attempt NOW” button. Then, at that point, give your email and subtleties to the enrollment interaction.
- When the enlistment page, SpyBubble will likewise request that you pick an appropriate membership plan. Guarantee you select an Android membership plan.
- Then, at that point, you will get an email with every one of the guidelines to set up the SpyBubble on your gadget. And even better yet is there also some kind contact form! Click here in order not only signup but setup such important details as credit card info (with no payment due), country code, billing address, etc…and follow all instructions they send out before actually making something official happen via phone or emails/text message from them while we are able? So enjoy our complete guide below covering how this functionality works.
Stage 2: Prepare the Device for Installation
You need to redo a few highlights to guarantee the establishment cycle works out in a good way. The particular things to perform include:
- Open the Play Store application on the objective gadget.
- When you dispatch it, click on the “Cheeseburger symbol” on the passed on piece of the menu to show the route.
- Through the menu, pick “Play Protect” the go to the settings by tapping the little stuff symbol in the upper right part of the menu interface.
- Then, at that point, guarantee you switch every choice under the “Play Protect” segment, and this is the thing that you should see:
- Check applications with Play Protect – Disabled.
Worked on unsafe application discovery – Disabled. Click OK button just until everything looks stable; when all these checks work well, press ‘OK’. Then verify if any malicious software or system calls are found during installation process (for example rootkit detected). If necessary, cancel install order based upon such detections so an updated app can be delivered faster/better into future releases. On Android 6+, ensure other types like USB drivers have been installed correctly & verified before proceeding. Install latest version available from official Google store which includes updates as long they were reported not working properly via normal device management tools including App Locker / Systemd status bar notification etc. Check compatibility checkbox whenever possible once your device.
Stage 3: Download and Install SpyBubble on the Target Device
You need to introduce SpyBubble on the objective gadget utilizing the right advances. These include:
- Open your favored program on the objective telephone and enact the Incognito Mode work.
- Reorder the download connect from the SpyBubble dashboard on the location bar, and snap enter. Doing with will open the SpyBubble APK on the objective gadget.
- Then, at that point, snap to open the downloaded record, and afterward click on the “Introduce” button. Then, at that point, sit tight for the establishment interaction to finish.
When you introduce SpyBubble, click on “Open” to enact the application. Upon entering in form fields of desired information (such as email addresses) it checks whether or not one is available, allowing the app access to all records acquired via an existing connection – even if they were already present prior when this was installed by using a pre-existing phone line! It then automatically establishes new contacts whenever necessary depending upon current Wi+d connections so long these remain active after any changes made before attempting to commit them directly across devices!. In other words; Once introduced into conversation like many modern apps do today its effectiveness becomes vastly improved because just about everything can be done within several seconds without fear of accidentally being discovered.
Stage 4: Complete The Setup Process on the Target Phone
SpyBubble should now be completely practical on your gadget, and this is the ideal opportunity to design the application’s capacities. Doing this will give you every one of the consents to guarantee the application capacities.
To begin, the following are not many interesting points:
- Tap on “Concur and Continue” on SpyBubble’s first screen to support the terms of administration prior to finishing the establishment cycle.
- When you acknowledge the EULA expressions, SpyBubble will request that you initiate the Keylogger work. Click on “Empower Keylogger Tracking” button to get to the availability menu.
- In the “Downloaded Services” area, click on “Client Accounts” and enact the switch work on the User Accounts Section. Then, at that point, click “Alright” on the screen that surfaces to give you admittance to the telephone activities.
- In the wake of actuating the keylogger, the application will find out if you need to continue with the programmed arrangement methodology. Sit tight for the break to pass, and afterward click on the manual methodology as past.
- Then, SpyBubble will look for access authorizations needed for the application. Actuate the capacity by tapping on “Award Permissions.” Then, click on ” Allow” on each assent the applications looks for on the approaching popup page.
- On the following screen, click on “Upgrade Stability” and afterward tap on “Permit” on the accompanying menu that surfaces. Doing this will guarantee the application capacities with practically no limitations and in secrecy mode. We’ll talk about these when we have further details…
- Subsequent to altering the strength settings, click on “Forestall Uninstall,” and afterward initiate “gadget administrator application.” Doing this will give SpyBubble consent to get to other applications, so they never undermine its capacities.
- On the following screen, click on “Empower Display Recording” and on the following actually look at box that shows “Don’t show once more” prior to tapping on “Start currently.” Doing this will allow SpyBubble to catch screen captures from the Android gadget. After doing it some time SpyBar can be used as a real camera in place of phone recording app or web-enabled webcam (and hence should stay off). If you are not sure about spybar your best idea is disable WiFi mode by going to preferences under main window tab; if enabled again wifi icon still displayed but does nothing!
Also change setting called “No Internet Access In Smartphone”. This allows an encrypted version for data transmission without internet connection after which all sensitive info stays recorded here because there’s no need anymore sending anything since we already have access to Google Earth with GPS location available every step of way too!.
Stage 5: Verify Setup and Start Monitoring
The last advance in the establishment interaction. Through this capacity, you decide if to utilize the application in secrecy mode or not. You need to utilize the code got during the application arrangement cycle and snap on “Complete Registration.” The application establishment interaction should now be finished.
Introducing SpyBubble on iOS
The application is easy to set up on iOS gadgets when contrasted with Android. That is on the grounds that you just need iCloud accreditations to get to an iOS gadget. Then again, Android gadgets require actual admittance to the gadget.
Luckily, you will not need to play out an escape interaction assuming that you have the iCloud accreditations of the gadget.
Star TIP – Ensure that you impair the 2-factor validation on the objective gadget. For most cases it seems like your goal here was to validate a device identity (the access token) so as well make sure its address isn’t spoofed by accident after gaining authorization from Apple for accessing apps through iMessage. This requires two things – A 1-2 factor authentication using Auth0 + AuthenticationKit which needs both 3rd party verification such As can still happen over wifi but only one at each edge route /device connected Alternatively there may also come about another requirement… Your primary use case… And then some other applications might depend on these requirements
Prerequisites
- iCloud accreditations of the objective iOS gadget.
- A checked SpyBubble record and membership plan.
Stage 1: Create an Account and Choose a Subscription Plan
You really want a free client account that is confirmed and approved with an appropriate membership plan. Give subtleties, for example, your email and secret key to enlist. You will get an email with a check interaction to finish the cycle.
Stage 2: Provide the iCloud Details
On your SpyBubble account, give the iCloud accreditations of the gadget. It’s a remarkable cycle from Android since you don’t require actual admittance to the gadget. Nonetheless, the 2-factor code confirmation include implies that you need to affirm the code you get from Apple. Therefore there can be zero trust in not having this verification process done as part (most likely)of submitting app or store information online via secure connection when using cloud services like iMessage or MailChimp. I’d suggest only enrolling one device without verifying others at first! We’ll have another blog post on how to do all these steps once we’ve received our credentials but now lets proceed immediately…
Stage 3: Login To Your Account and Start Monitoring
At the point when the arrangement is finished, visit the dashboard and hang tight for it to transfer client information. The cycle may take some time, particularly assuming that the objective gadget doesn’t have a steady web association.
Once the application begins transferring the information, you will approach all the substance that SpyBubble can follow. For example there are three components of an encrypted email sent on your behalf by Facebook Messenger. We’ll concentrate here on how this works directly with our system – although we could add more elements based upon what customers want. This process takes approximately one day depending in part because many users haven´t yet got familiarised enough about HTTPS (HTTP) protocol at home to use services like spybuble – especially since they cannot connect securely between these two protocols via SSH as per Twitter’s instructions or other VPNs (the latter however still might work fine).
Pros and Cons
Pros
- Generally reasonable
- Clean and easy to use UI
- Root/escape not obligatory
- Imperceptible
- Quick information synchronizing
- Easy to utilize
- Shows application use continuously
- Full admittance to Instagram and Facebook
Cons
- iCloud certification needed for iOS
- No geo-fencing
A few elements are iOS-restrictive like: photos with a maximum of 10,000 views; “approved” posts that have been shared within the last 24 hours. It seems quite vague on this point so I thought some more before jumping into it..
What will be implemented is an opt in system where if you approve anything – which isn’t necessarily necessary but hey does make sense at least when everyone’s mobile devices can work together! Once approved your post could reach millions and then all things being equal should get seen by tens of thousands…it’ll also only show up via notifications (though possibly other features too).
Is it Possible to Install SpyBubble Remotely?
Indeed, it’s feasible to introduce SpyBubble from a distance. All you really want is to enter your iCloud subtleties on the objective gadget. Besides, Android clients will require one-time actual admittance to the objective gadget. Doing this will give the application the essential authorizations to work.
How Often Does the App Update Information From the Target Device?
The application refreshes data from the objective application later like clockwork consequently. All things considered, you can tweak the update stretches and information inclinations. The recurrence update likewise relies upon the reinforcement execution.
What number of Devices Can I Track?
You can follow a few gadgets utilizing your SpyBubble record. All things considered, SpyBubble allows you to interface and unlink for quite a long time. The main issue is that you can just connection each record in turn. Along these lines, you have a few gadgets. Of course there are some exceptions too but after all, most people opt out when they discover privacy issues by creating spy devices at home or abroad. But what about other applications based on iOS technology? This was clearly mentioned many times as well! In fact, Apple also put its stamp directly on both OSX and iDevices using their frameworks such Google Play Services. As per an earlier blog post ( http://www.sibbingshare ) even if device identifiers aren’t used remotely between apps within iPhone only use SSO protocol with default credentials should be good enough during setup/recording since everyone always remembers them very easily…
Would i be able to Track My Apple Device Without an Apple ID and Password?
Indeed, you can follow your apple gadget without an ID and secret phrase. You need to acquire actual admittance to the objective telephone prior to getting to any information identifying with a particular client account.
Would i be able to Monitor an iPhone Without an Apple ID or Password?
No, you can’t screen an iPhone without setting up an Apple ID or secret key. The best arrangement is gain actual admittance to the gadget. Doing this will furnish you with moment admittance to your favored gadget.
Is the SpyBubble Icon Visible After Setting It Up on Android?
Indeed, the SpyBubble symbol may in any case be noticeable even in the wake of setting it up on Android. You might need to get to the application first to assist with utilizing it in secrecy mode. Nonetheless, iOS clients have it contrastingly on the grounds that the application doesn’t need actual establishment. For android they just see the icon alone as well as display only two messages: “Welcome To Private” and so forth. But after some other processes are completed (e 2Ghz network connection etc.), then more accurate security becomes possible here along not merely sending private/confidential data but giving all sorts potentially sensitive info like credit card number under PIN-protection code + unique identifier plus password(s). Your friend isn´t going anywhere until he has been successful for 30 seconds at using his phone himself!
Conclusion
Like the work your people played, you must find methods of ensuring your kids foster right. The web is another contraption that has simplified life, yet then again it’s a broadly perilous spot for thoughtless people like youths or kids.
Push ahead in getting your child’s devices and security by presenting applications like SpyBubble. The application is solid and simple to use. It doesn’t have some fancy features but gives ideas about how children might access things on our networks without requiring all sorts from us so much. Of course other apps exist outside these categories such as Pwnit, which allows parents who want to learn more before they put their son at risk can do this too using code written very efficiently with no malware attached. All-in there are reasons why teenagers should watch out for vulnerabilities found through websites (this happens every day) while an app would bring back something useful only if we had full information – always better than letting bad guys sneak into someone else user’s home network undetected!